As more organisations have moved to Microsoft Azure AD and Intune to manage their devices a common request is how to integrate this with Aruba ClearPass, which handles the RADIUS requests for Network Access Control. The most common deployment pushes certificates to the clients which use these for EAP-TLS authentication with ClearPass. Note this post doesn’t cover the basic Intune integration setup which is documented in an Aruba guide.
But you probably want to know whether a bit more about the client than whether it has a valid certificate, so ClearPass has an Intune extension which will download information from an Azure tenant’s Intune to the Endpoints Repository database.
This allows you to make policy decisions based on Intune attributes, such as compliance state, allowing you to place clients in different roles/vlans depending on what the client is, whether it’s compliance with policy, department, etc etc.
However… the Endpoints Repository uses MAC addresses so problems start if clients are using MAC randomisation. The MAC address presented by the client won’t match what’s recorded by Intune so it won’t be possible to match against Intune attributes in the Endpoint.
The first thing to do is stop using the MAC address as the UID. Much better to use the Intune ID and have this written into the client certificate, either as the CN or a SAN though you can use any variable that ends up computed from the authentication.
You can then either query Intune directly using the Intune Extension HTTP method or use the Endpoints Repository in a slightly different way.
I prefer the latter option most of the time because it provides a level of resilience as well as improving performance. Querying the Intune API via the extension works very well but if Intune is down (which has been known to happen) that won’t work. It will also take longer than querying a local database.
ClearPass assumes you’re using the presented MAC address as the UID of the Endpoint and it isn’t possible to change this. Instead you can query Endpoints as an SQL database with a filter that pulls out the attributes you require based on the presented certificate CN.
ClearPass databases can be accessed externally using the username ‘appexternal’ and the password which is set in cluster-wide parameters under the Database tab.
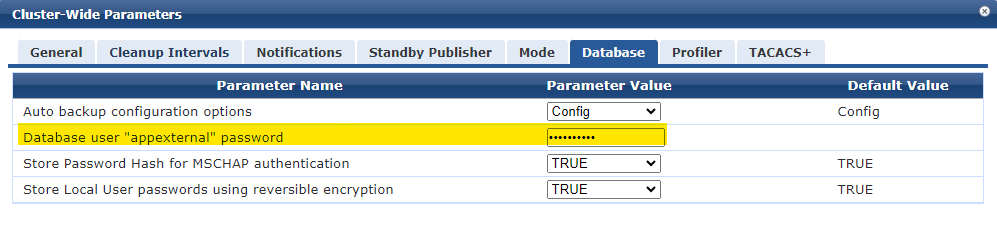
Next create a new Generic SQL DB Authentication source pointing to the local tipsdb and set a filter that pulls out the attributes you want for the auth session variable presented.
Server name: <server IP>
Databse Name: tipsdb
Username: appexternal
Password: <password you set>
ODBC Driver: PostgreSQL
Password Type: Cleartext
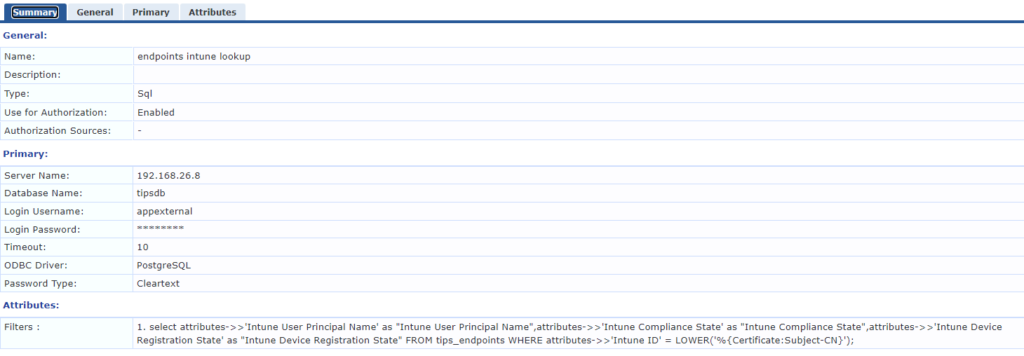
A few things to note here. You can’t use localhost as the server name. If you have a VRRP address you can use this, otherwise you must use the actual IP of the server. This can cause complications in an environment with multiple ClearPass servers and no VRRP. There are ways around this but that’s for another blog.
The filter is the SQL query that pulls out the attributes you want based on an attribute presented. In this case we’re selecting ‘Intune User Principle Name’, ‘Intune Compliance State’ and ‘Intune Device Registration State’ for a record where the ‘Intune ID’ matches Subject-CN of the client certificate
select attributes->>'Intune User Principal Name' as "Intune User Principal Name",attributes->>'Intune Compliance State' as "Intune Compliance State",attributes->>'Intune Device Registration State' as "Intune Device Registration State" FROM tips_endpoints WHERE attributes->>'Intune ID' = LOWER('%{Certificate:Subject-CN}');You then specify for each of these how you want the system to use the data it gets back, essentially either as an attribute or directly set as a role.
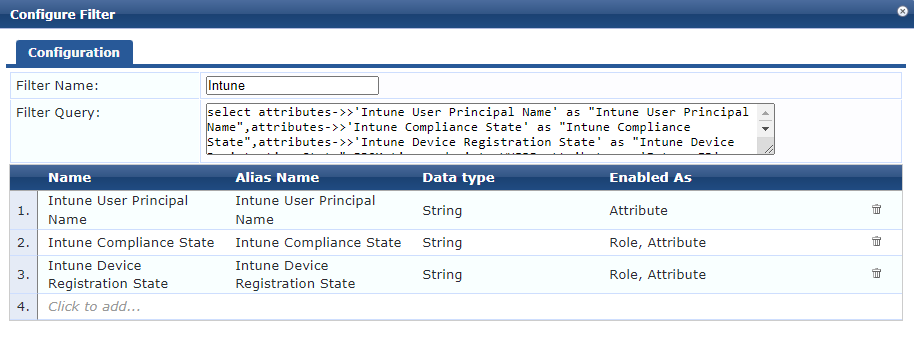
Add your custom authentication source into the service, and you’re good to go. You will now be able to make policy decisions based on the Intune ID lookup rather than the MAC address.
Three more things to note about this.
If you’re limited as to what can go into the certificate CN or SAN you can use the same method to pull out other details, for example with a query like this:
select attributes->>'Intune User Principal Name' as "Intune User Principal Name",attributes->>'Intune Compliance State' as "Intune Compliance State",attributes->>'Intune Device Registration State' as "Intune Device Registration State" FROM tips_endpoints WHERE attributes->>'Intune Device Name' = '%{Authentication:Full-Username}';This method requires the device to be in downloaded to Endpoints by the Intune Extension. If that doesn’t happen it won’t be there to match on. In some circumstances Intune no longer records MAC addresses for devices – notably self-registered personal Android devices – and because the Endpoints Repository is based around MAC address these devices will be missing.
This is one of the reasons it’s worth using the Intune ID as your device’s UID in the certificate – if you need to query the Intune extension via HTTP you’ll need to present it with the Intune ID, nothing else will work. It’s worth noting devices will also have an Azure AD ID which looks similar, and will likely be the same for devices not managed by Azure AD, but the Intune API only understands the Intune ID when querying for device attributes.

Hi – So how do we setup clearpass to query intune ONLY if it cannot find the device or a certain attribute from the periodic sync?
Chances are intune doesn’t have a MAC address for the device, so it will never sync with the endpoints repository. You need to query the Intune extension over http – as documented – and pass it the intune id which will directly query intune. You therefore need to have the intune id within the certificate presented by the device. So my advice is always make sure the intune id is included. Note that for devices that are not azure AD, e.g. BYOD android phones, the azure AD ID and the intune ID will be the same… however for any AD connected devices these will be different. It’s the intune ID you have to present for auth.
You mentioned “A few things to note here. You can’t use localhost as the server name. If you have a VRRP address you can use this, otherwise you must use the actual IP of the server. This can cause complications in an environment with multiple ClearPass servers and no VRRP. There are ways around this but that’s for another blog.”
Any suggestions on work arounds for when you have multiple Clearpass servers with no VRRP?
I think your options are to use a VIP provided by an external load-balancer. Alternatively you would need to setup separate services for each server, each with its own database lookup to the local server IP, and then select service based on server connection. That’s quite inelegant but you would be able to share role-mapping and enforcement policies across the services – it just means that any service changes would have to be replicated.
Having the client certs containing the inTune ID is so much easier if you can make it happen.
Hi,
I’ve configured the query below in our ClearPass enviroment.
select attributes->>’Intune User Principal Name’ as “Intune User Principal Name”,attributes->>’Intune Compliance State’ as “Intune Compliance State”,attributes->>’Intune Device Registration State’ as “Intune Device Registration State” FROM tips_endpoints WHERE attributes->>’Intune ID’ = LOWER(‘%{Certificate:Subject-AltName-URI}’);
The device ID in Azure is being set in the Subject-AltName-URI of the certificate. This is the only difference from your query.
In the logs I am receiving the error below when authenticating a Intune device.
2024-11-15 10:04:01,276 [Th 211663 Req 178029571 SessId R01076f88-02-67370e81] INFO RadiusServer.Radius – rlm_sql: trying to reconnect
2024-11-15 10:04:01,287 [Th 211663 Req 178029571 SessId R01076f88-02-67370e81] ERROR RadiusServer.Radius – rlm_sql_unixodbc: sql state – 42601, sql error – ERROR: syntax error at end of input; Error while executing the query
2024-11-15 10:04:01,287 [Th 211663 Req 178029571 SessId R01076f88-02-67370e81] ERROR RadiusServer.Radius – rlm_sql_unixodbc: SQL down 42601 ERROR: syntax error at end of input; Error while executing the query
We’re running ClearPass version 6.12.3. Any ideas?